In the upliftment of digital world, cyber-attacks have emerged as a critical commination to individuals, businesses, and governments as well. Considering the prevalence and sophistication of the underlying attacks, understanding the landscape of cyber threats and the measures to defend against them has never been more crucial.
Attribute of Cyber Attack
A cyber-attack is any attempt by anomalous or unauthorized access to damage or disrupt the seamless working of cyber space, networks, or devices. These attacks can target individuals, private companies, public organizations, and critical infrastructure, with motives ranging from financial gain to political agendas.
Common Types of Cyber Attacks
- Phishing Attacks: Phishing is a social engineering attack where attackers aim to misguide individuals into revealing sensitive information, such as usernames, passwords, and credit card details. This is typically done through ambiguous emails, messages, or websites that appear legitimate.
- Malware: Malware encircles various malicious software, including viruses, worms, ransomware, and spyware. On installation, malware can breach data, damage systems, or maliciously control the infected device.
- Ransomware: A ransomware is a type of malware that encrypts a victim’s data and demands payment (usually in cryptocurrency) to re-establish access. The large organizations with high profile have experienced the severe impact of ransomware.
- Distributed Denial of Service (DDoS) Attacks: DDoS attacks maliciously control a target’s network or website with a overflow of internet traffic, making it inaccessible for the valid user. These attacks often grasp large numbers of compromised devices (botnets) to amplify the invasion.
- SQL Injection: This attack injects anomalous SQL code into a database query, permitting hackers to influence and access data in a database. Faultily secured applications on web are significantly vulnerable to SQL injection.
- Zero-Day Exploits: Zero-day targets and destroys prior unrevealed anomalies in software. Since there’s no previous knowledge available, these attacks might be significantly blaming.
Case study of cyber-attack: 2024 MOVEit Transfer Data Breach
In 2024, the MOVE it Transfer software, an extensively used solution for file transfer, was targeted by a particular cyber-attack. The data theft adversely effected numerous organizations globally, concentrating vulnerabilities in protected data transfer solutions. Noteworthy frequency of sensitive data was breached, exponentially leading to identity theft, financial loss, and intellectual property theft. The estimates commended the breach could affect the organizations cost inclusively over $500 million in destruction, including rectifying costs, administrative fines, and other business loss.
Eye-Opening Cyber Attacks benchmarked in 2024:
The graph visualizes the devastating nature and frequency of cyber-attacks in 2024:
- Regular Occurrence: 2200 attacks
- Annual Uplift: 15%
- Ransom Cost: $1.85 million
- Retrieval Cost: $4.5 million
- Data Revealed: 22 billion
- Cost of Data Violation: $4.35 million
- Phishing Ubiquity: 82%
- Phishing that targeted businesses: 76%
- Financial Calamity: $10.5 trillion
- Interruption: 21 days
- Zero-Day Abuse Escalation: 33%
- Uplift in Supply-Chain Attacks: 42%
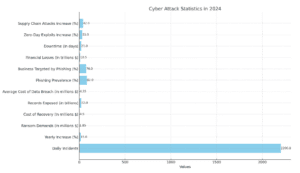

This visualization illustrates the noteworthy influence and heighten threat of cyber-attacks, accentuating the requirement for vigorous parameters for cybersecurity.
Master Plan for Protection: The key strategies that contribute to control the threat of cyber attacks are as listed below:
- Educating and Awakening employees
- Vigorous solution for security
- Breakthrough Threat Recognition and Reaction
- Systematic and Uniform Backups
- Distribution of Network
- Cyberattack Retaliation Plan
Learn to navigate the digital battlefield with our guide on understanding cyber-attacks. Explore common attack types, 2024 incidents, and strategies to safeguard your data. Discover more at Karnavati University’s B.Tech. Computer Science and Engineering with specialization in Cyber Security.
By: Anamika Singh
Assistant Professor, UIT, Karnavati University






